Cisco
Unity Directory Access Diagnostics Contents
Requirements
and Special Notes
Resolving
Property Access Test Failures
Resolving
User Creation Test Failures
Resolving
Mailstore Access Test Failures
Overview
The Cisco Unity Directory Access Diagnostics tool (DAD) checks the Cisco Unity Directory Service account’s permissions to import, manage, or create a single Active Directory user object.
DAD also checks the Cisco Unity Message Store Service account’s permissions on Microsoft Exchange 2000 and Exchange 2003 mailstores.
DAD provides three basic tests:
Requirements
and Special Notes
![]() DAD is for use with Cisco Unity deployed in a
Microsoft Exchange 2000 and Exchange 2003 environments only.
DAD is for use with Cisco Unity deployed in a
Microsoft Exchange 2000 and Exchange 2003 environments only.
![]() DAD must be run on the Cisco Unity server and is
designed for use with Cisco Unity 3.1 and later.
DAD must be run on the Cisco Unity server and is
designed for use with Cisco Unity 3.1 and later.
![]() To use DAD, you must log onto the Cisco
Unity server as the account configured as the logon account for either the
Cisco Unity AvDSAD. DAD will not run if
you are logged in as any other user.
To use DAD, you must log onto the Cisco
Unity server as the account configured as the logon account for either the
Cisco Unity AvDSAD. DAD will not run if
you are logged in as any other user.
User Access Test
DAD’s User Access Test will test a single Active Directory account that you select.
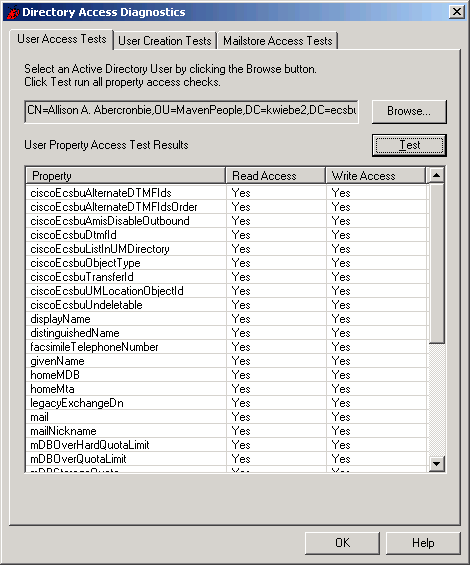
Figure 1
Select an Active Directory user object by clicking the Browse… button.
When you click the Test button, DAD will perform access checks on individual attributes of the selected user object.
The results of each access check are displayed on the User Access Test dialog.
Yes means the Cisco Unity Directory Service Account has necessary permissions.
No means the Cisco Unity Directory Service Account does not have necessary permissions.
Failed means DAD could not determine whether or not the Cisco Unity Directory Service Account has necessary permissions. Check DAD’s log files for diagnostic error information. See Logging.
Double-click any property to display a help offering guidance on resolving any permissions issues.
Note: Be sure to check the results for read and write access tests on all properties. You may need to scroll the display to see the results of all tests.
Take special note of a possible warning that may appear at the bottom of the results dialog, as shown in the figure below.
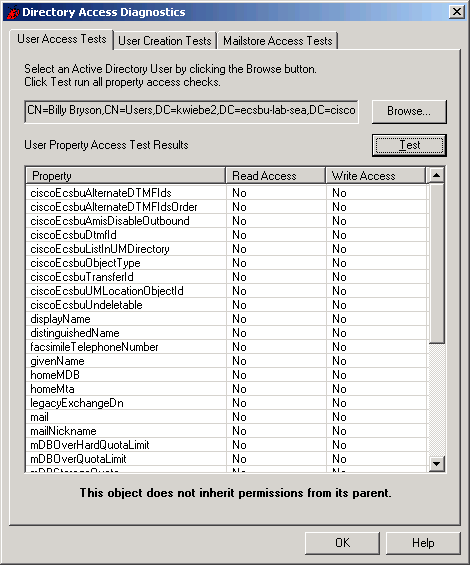
Figure 2
If a user object does not inherit permissions from its parent object, such as an organizational unit, permissions required by Cisco Unity service accounts to access that user may not be applied on the user object. Cisco Unity Permissions Wizard grants permissions on organizational units and depends on inheritance for application of those permissions on user objects.
Resolving Property Access Test Failures
Most Object Access Test failures can be resolved using Active Directory Users and Computers. ADSIEdit may be required to modify permissions for some properties.
Open the Properties for the Active Directory user object you are testing access to, choose the Security tab, click the Advanced… button, and click the View/Edit… button to examine permissions that affect the Cisco Unity Directory Services Account. Property permissions appear on the Properties tab. Access to an individual property may be allowed or denied to the Cisco Unity Directory Service Account itself, or to a group the Directory Services Account is a member of. For example, the Cisco Unity Directory Services Account is a member of the local Administrators group. Be sure to check permissions for the Directory Services Account and all groups that the Directory Services account may be a member of.
Access to an individual property may be allowed or denied in several ways:
![]() Read/write permissions for property itself
Read/write permissions for property itself
![]() Read/write permissions for a property set that
includes the property
Read/write permissions for a property set that
includes the property
![]() Read/write permissions for all properties.
Read/write permissions for all properties.

Figure 3
Ensure that all appropriate permissions are granted. Some properties may be reflected in more than one way in the Active Directory Users and Computers security management dialogs. See specific help for each individual object access test in Cisco Unity Directory Access Diagnostics User Access Tests. Refer to Active Directory documentation for advanced help on setting access rights on Active Directory objects.
If DAD has reported that “This object does not inherit permissions from its parent”, open the Properties for the Active Directory user object you are testing access to, and choose the Security tab. The checkbox labeled “Allow inheritable permissions from parent to propagate to this object” will be unchecked. Check the checkbox to enable permission inheritance.
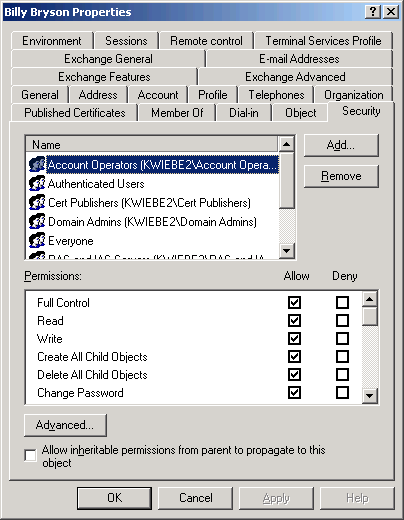
Figure 4
Note: If the user you are checking is a member of a security group, such as Domain Admins or Enterprise Admins, Windows 2000 or 2003 may be disabling permissions inheritance automatically for the user. See the following Microsoft Knowledge Base articles for details on this process:
http://support.microsoft.com/default.aspx?scid=kb;en-us;318180
http://support.microsoft.com/default.aspx?scid=kb;en-us;81743
If the user you are testing is affected by this Windows behavior, you will need to grant permissions necessary for Cisco Unity on the user object itself, rather than relying on inheritance from its parent container.
User Creation Test
DAD’s User Creation Test will test the creation of a single user in the Active Directory container you have chosen as the default container for new Cisco Unity subscribers.
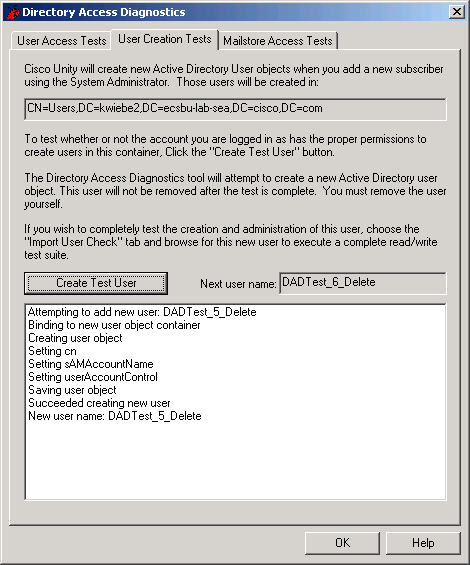
Figure 5
The container in which the new user will be created is displayed near the top of the dialog. By clicking the Create Test User button, a new user will be created with the name displayed in the Next user name field. Figure 5 shows the results of adding s single user named DADTest_5_Delete, and ready to add another user, DADTest_6_Delete. The name of the user is designed to remind you that it’s a test user, created by DAD, and that you can, and should, delete it.
Note: DAD will not delete its own test users. You must do that yourself.
If, after creating a test user, you choose the User Access Tests tab, the newly created user will be automatically ready for testing of all other access rights.
Double-click any line in the results list to display a help page offering guidance on resolving failures.
Resolving User Creation Test Failures
User Creation Test failures can be resolved using Active Directory Users and Computers or ADSIEdit.
Open the Properties for the container where new users are created, as displayed on the User Creation Tests page, choose the Security tab, click the Advanced button, and examine the permissions for the Cisco Unity Directory Services Account on the Object tab. User creation rights may be allowed or denied to the Cisco Unity Directory Service Account itself, or to a group the Directory Services Account is a member of. For example, the Cisco Unity Directory Services Account is a member of the local Administrators group. Be sure to check permissions for the Directory Services Account and all groups that the Directory Services account may be a member of.
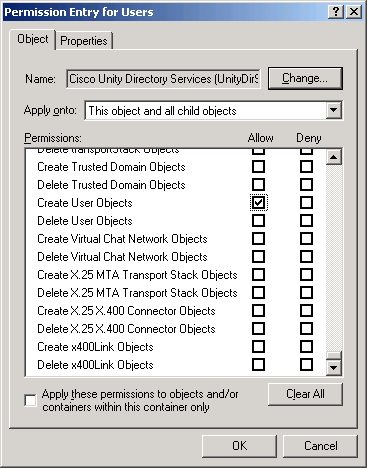
Figure 6
Ensure that the Cisco Unity Directory Services account, or some group the Directory Services Account is a member of, has permission Create User Objects in the container, and that there are no specific denials of Create User Objects permission for the account or any groups it may be a member of. When in doubt, explicitly grant Create User Objects permission to the Directory Services Account, and ensure no denials to Create User Objects exist.
You may also examine DAD’s diagnostic logs for more
information about the failure. See Logging.
Mailstore Access Test
DAD’s Mailstore Access Test will test Microsoft Exchange 2000 and Exchange 2003 mailstores that you select to determine if the Cisco Unity Message Store Service account has sufficient access to perform its messaging functions.
Select the Microsoft Exchange 2000 and Exchange 2003 mailstores you would like to test by clicking the Select mailstores… button.
When you click the Test Mailstores button and provide the password for the Cisco Unity Message Store Service Account, DAD will perform access checks on each mailstore you have selected.
The results of each access check are displayed on the Mailstore Access Tests dialog.
Yes means the Cisco Unity Message Store Service Account has necessary permissions.
No means the Cisco Unity Message Store Service Account does not have necessary permissions.
Failed means DAD could not determine whether or not the Cisco Unity Message Store Service Account has necessary permissions. Check DAD’s log files for diagnostic error information. See Logging.

Figure 7
Resolving Mailstore Access Test Failures
Most Mailstore Access Test failures can be resolved using Microsoft Exchange 2000 System Manager. ADSIEdit may also be used.
To modify Microsoft Exchange 2000 or Exchange 2003 mailstore permissions using the Microsoft Exchange System Manager, you must first add the ShowSecurityPage entry to the registry, which then displays the Security tab in mailstore Properties dialog boxes. The Security tab does not appear by default, so you must first make this registry change.
To add the ShowSecurityPage entry to the registry:
- On the Start menu, click Run, type regedit, and then click OK.
- Locate the following key in the registry: HKEY_CURRENT_USER\Software\Microsoft\Exchange\ExAdmin.
- To add the ShowSecurityPage DWORD value, click Edit, click New, and then click DWORD Value.
- For the new value name, type: ShowSecurityPage
- Double-click ShowSecurityPage, and in Value data, type: 1
To check mailstore rights using Microsoft Exchange System Manager:
- Start System Manager: On the Start menu, point to Programs, point to Microsoft Exchange, and then click System Manager.
- Expand the tree to display mailstores, as shown in the figure below.
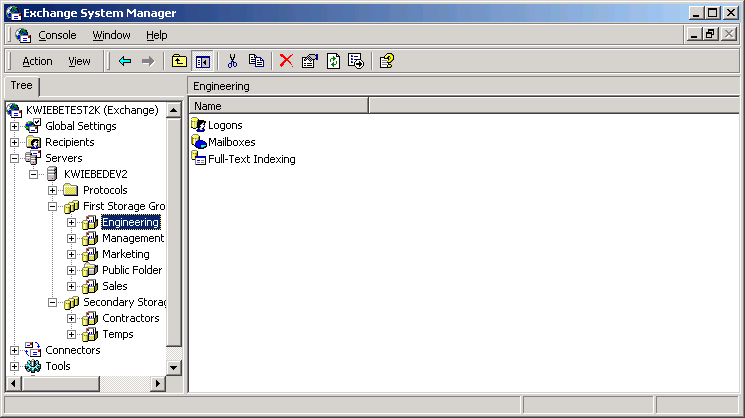
Figure 8
- Right click the mailstore you are interested in and click Properties.
- Click the Security tab.
- Confirm that the Cisco Unity Message Store Service Account has been granted Administer Information Store, Send-As and Receive-As rights, as shown below.
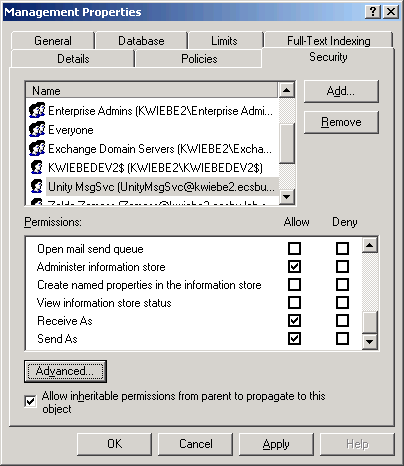
Figure 9
The Cisco Unity Permissions Wizard can be used to grant Administer Information Store, Send-As, and Receive-As rights if you choose not to do it manually.
Logging
DAD generates a diagnostic log file that contains detailed information about errors encountered during operation.
The file DirectoryAccessDiagnostics.log will be created in the temp directory of the Cisco Unity Directory Services Account.
For example, if your Cisco Unity Directory Services Account is UDirSvc, the file would be:
C:\Documents and Settings\UDirSvc\Local
Settings\Temp\DirectoryAccessDiagnostics.log
Revision History
1.0.0 – Initial version.
1.2.0.1 – First released version
1.2.0.2 – Minor help revisions and
cosmetic defect fixes.
1.2.0.3 – Fix display of version in
about box.
1.2.0.6 – Add mailstore access
checks, remove unnecessary object access checks, enhance logging
1.2.0.9 – Change create user test
to create disabled users.
Version 1.2.0.10,
1. Defect fix: CSCed49761
Version 1.2.0.11,
2. Accomodate move of Directory Connector registry information to SQL database
© 2004 Cisco Systems, Inc. --
Company Confidential